I use a VPN service to secure my Internet traffic against potential eavesdropping from my government. I plan to write a post on why I choose to do so (VPN services are a debatable topic), but for the moment I just want to sketch a simple procedure to prevent DNS leak when using OpenVPN with systemd-resolved.
I know there’s a project update-systemd-resolved to address that issue, but I wanted to keep it as simple as possible and avoid having to maintain an ad-hoc external integration.
There’s basically two places where you need to update DNS servers:
/etc/resolv.confresolvectlfor the interface connected to your Internet gateway
The first one is trivial, you just need to modify a text file.
For the second one, you need first to identify the correct interface, in my case br1, which is link number 9:
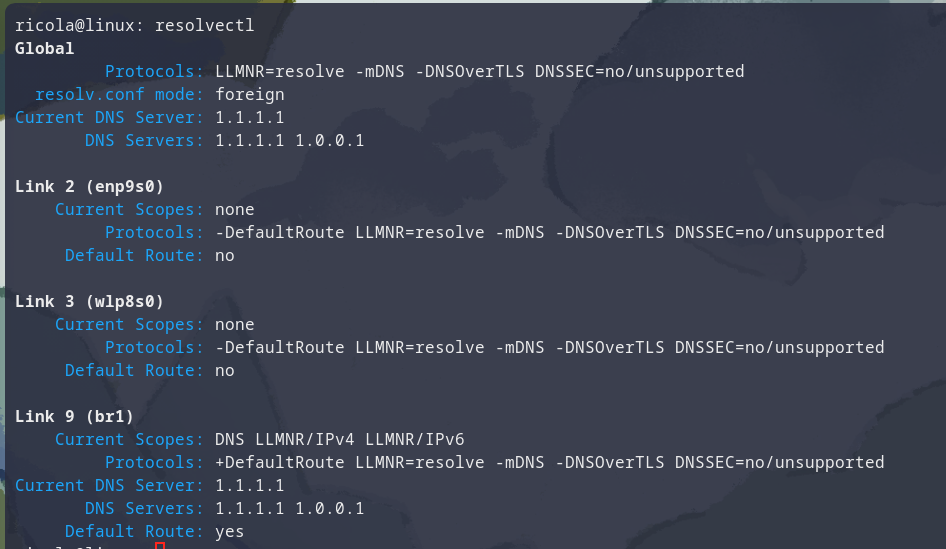
To change DNS for Link 9, I need to issue the following command (run as su):
resolvectl dns 9 <dns-ip-address>And eventually flush cache:
resolvectl flush-cachesI wrote a minimal script to streamline setting up/down the config:
#!/usr/bin/bash
linknum=`resolvectl | grep br1 | awk '{ print $2 }'`
dns_vpn="<dns-from-vpn-provider>"
dns_cf1="1.1.1.1" # I use cloudflare public DNS
dns_cf2="1.0.0.1"
if [ -z "$1" ] || [ $1 = 'up' ]; then
echo 'ENABLING'
echo "nameserver $dns_vpn" > /etc/resolv.conf
resolvectl dns ${linknum} $dns_vpn
elif [ $1 = 'down' ]; then
echo "DISABLING"
echo -e "nameserver ${dns_cf1}\nnameserver ${dns_cf2}" > /etc/resolv.conf
resolvectl dns ${linknum} ${dns_cf1} ${dns_cf2}
fi
resolvectl flush-caches(Of course, you will have to change linknum variable to adjust to your setting)
Leave a Reply